Preamble
The world of cybersecurity is a lot bigger than most people think. Some outsiders believe it to be this glorified hacking collective. Others view it as just IT , perhaps on steroids if they’re more open minded. And a few think it’s just utterly useless and security is a fugazi, to which I say GG NO RE, good luck on your adventures. Whatever your mindset is, this page is intended to help folks figure out a possible way into the cyber realm.
Why do I know this stuff? I have a background that consists of time in the military, a three letter federal agency, an old monolith corporation, a young startup, a tiny firm, and one of the world’s leaders in cyberspace (which was later acquired by a Fortune 10 company). I also started my own consultancy, hired people, did random computer-related volunteer work, and dabbled with IT -type tasks since I was a kid. At this point, my career is as high as it can go for a non-manager, and the foundation of my personal understanding of cyber is completed.
Note that the field has so much in it and evolves so much that anyone claiming to be a “total expert” or know just about everything is full of 💩. The best you can get to is knowing so much about the very basics that you can understand any concept or navigate any task/threat with someone who specializes in that specific subset of work. I promise that if you like think your “programming prowess is so high you’re the bees knees in cyber so you know it all,” you’ll never understand risk management cycles at a CISO level or budget implications for tool procurement. Why do you need to know the basics about this stuff? Well, good luck getting anywhere in the corporate world without it. Federal is a different story, you can get away with being an expert in just one specific function, but I genuinely pray your job never goes away or gets drastically transformed.
Disciplines
The first and most important thing to figure out is which discipline you want to specialize in. Being a wildcard serves you no good, trust me on that one. Do keep your skillset nice and wide, though, but focus your efforts on a specific role. Ultimately, the start of your career will likely be dynamic, especially if you’re reading this page. Seasoned specialists are unlikely to switch out of their role. For example, I’ve been in threat intelligence ( TI ) since day one, and over a decade later I have not left my specialty. That said, I have experience in Incident Response, SOC work, system administration, network monitoring, risk analysis, and a bunch of other fields.
A great starting point is the NICCS career pathways tool, which helps new and transitioning practitioners figure out what they want to do. Their micro-challenge site, TryCyber, helps get a better hands-on understanding of what these disciplines mean. NIST SP 800-181 is the framework document behind this information, consisting of 52 work roles and their descriptions. Powerful tool to understand what each role might do, kinda. Reality is very different, as every organization looks different. Honestly, no two places have been more than 80% same for me when it comes to role, even in the federal world.
In this image, we see five primary fields: IT, Cybersecurity, Cyber Effects, Intel (Cyber), and Intelligence. Additionally, four cross functional fields either support or augment the cyber workforce. Intelligence is a dotted line, as NICCS makes a distinction between “insert-name intelligence” and “cyber intelligence” while still understanding that a lot of intel functions feed into cyber. Human Intelligence (HUMINT), for example, is a great enabler for cyber effects by placing the right people at the right place and allowing for social engineering as an initial access vector. Likewise, a cyber effect can enable collection on a HUMINT target.
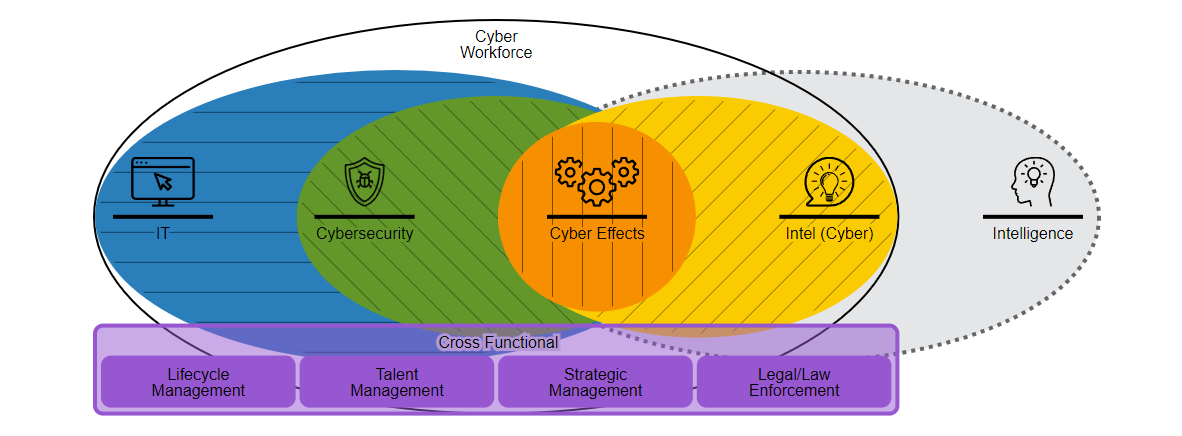
If the differences don’t make sense immediately, take some time to review each one.
- IT is the lifeblood of an interconnected infrastructure. Without programmers, developers, architects, and administrators, there is no cyber workforce as there is nothing to defend. Don’t forget that as you go through your journey – please don’t become a security elitist who looks down upon IT personnel.
- Cybersecurity is the love child of many different functions that ultimately act to secure a network. These include things like systems analysts, security architects, forensics specialists, incident responders, and certain managers.
- Cyber Effects is both a career field and an action. In this context, exploitation analysts, operators, planners, and developers craft effects (aka offensive cyber capabilities). Pretty much no one outside of very specific federal agencies falls under this field.
- Intel (Cyber) is just a weird way to denote CTI honestly. NICCS wants to break these out but I don’t so that leads me to item number 5…
- Intelligence, which encompasses just about any study of information. Not to be confused with “smarts” or brain capacity… Intelligence exists in many forms and covers a wide array of topics. Cyber practitioners use intelligence to understand what they need to defend or attack, how, and why. My earlier example of HUMINT covered one such venue.
- In corporate information security terms, intelligence provides you with context and prioritization to combat threats. Understand that Business Intelligence ( BI ) is not far removed from CTI , as just about anything you do in the private sector requires cold hard dollars behind it, meaning you need to explain why your work matters or solutions justified. – My motto here: “Creating a common operating picture using Business Intelligence derived from threat data.” I came up with this phrase when my consultancy clients had issues understanding the difference maker that CTI is. I draw on a BI analyst using market data to forecast sales and adjust inventory accordingly. With CTI , an analyst uses threat data to analyze cyber trends and inform defensive – Intelligence is massive though and has many different definitions. Work to move away from using “Cyber Threat Intelligence” in your dictionary, and instead say “Threat Intelligence”. Why? Because you are likely to fall into the trap of ignoring things that are not strictly signals – meaning, X attacked Y and we observed it directly so I wrote about it. For example, you can use geopolitical intel to observe regional issues that may impact a data center, thus adding risk to the network. CTI focused analysts often fail to consider the full breadth of data available to them and how a business leader may use it. To be clear, this is tailored for corporate thinking, because these questions don’t really exist in the federal sector.
Understand that “entry level” in cyber is effectively mid-level for a lot of other fields. This is not something you can just jump into, but it is something you can transition into with the proper work. You’re probably thinking that’s great and all, but how do you actually get into the discipline of your choice?
- Education. Some sort of education, even self-started, will put you ahead of a good amount of people. The higher quality and quantity, the more likely you are to eventually impress someone willing to give you a shot at gaining experience.
- Read the Education section below for what that includes.
- Internships. These are almost always reserved for high school to graduate level students. Some opportunities exist for those that are not. Fun secret: you can enroll into your local community college (or a nearby one) that has cyber classes and become eligible for some programs. It’s harder getting in this way and you really gotta impress the interviewer, plus need to make sure the requirements are not a four-year degree school.
- Cross-pollination. This is a harder one to pull off and requires patience, sometimes a lot of it. Start out in a more attainable field, such as sys admin in IT or gasp help desk.
- Cross-pollination is the hardest thing to get through. It may take many years and additional education to step through the rankings until you reach a cybersecurity position. Some examples I’ve seen include:
- Sys admin with 20 years and numerous online learning programs (Coursera, AWS, gCloud, etc) ended up in a SOC lead role after doing a great interview and having some prior employer overlap. From there, he rinsed through numerous organizations doing various SOC work until he landed in a Cloud Security Specialist role.
- Help desk team manager with 10 years of experience and great metrics ended up in a entry level security analyst role, taking a severe paycut but willing to learn. Turned out to be highly motivated and over the span of 2 years became the senior security analyst on the team.
Education
There are a number of courses and ideas when it comes to learning cyber-related. In my opinion, the best cyber education is honestly free. You can learn a ton from YouTube, StackOverflow, and even Reddit (r/netsec).
Certifications
Most certifications are… okay. In my experience, employers are decreasing how much weight these certs have, let alone even assessing the implications of each cert. Some positions demand these credentials, such as PMP for project managers or CCNA for government network engineers. Realistically, entry level practitioners should use certs for their academic advantage. That said, most certs are becoming money grabs. Take both content and credential to great scrutiny; especially if you’re spending doubloons on it!
My recommendations here for both professional development and “checking the box”:
- Google Cybersecurity
- This is a good starting point for people interested in learning more about cybersecurity. Entry level practitioners can also stand to gain insight through this course. Highly recommend checking it out before going further or enrolling in related college classes. 7 day trial is free, afterwards $49 per month AFAIK .
- Certified Information Systems Security Professional
-
CISSP
is one of those certs that you hear about and either think it’s S tier or it’s hot garbage. To be frank, it’s a huge “check the box” cert at this point. It holds some prestige for mid-level practitioners, and there’s also a great community behind it. Indeed shows around 1200 jobs in the United States and 200 jobs Remote that list CISSP.
- Certain government agencies require IAT/IAM Level 3, which CISSP fulfills both neatly. It is a great cert to have if you can afford it and you’re confident in your knowledge and experience. The bar to entry is rather high compared to most standard industry certs.
- A month of casual studying as a senior-level practitioner got me through this exam.
-
CISSP
is one of those certs that you hear about and either think it’s S tier or it’s hot garbage. To be frank, it’s a huge “check the box” cert at this point. It holds some prestige for mid-level practitioners, and there’s also a great community behind it. Indeed shows around 1200 jobs in the United States and 200 jobs Remote that list CISSP.
- Any GIAC certification
- While not a specific cred,
GIAC
as an entity has some of the highest respected professionals and content in the industry. I have three GIAC certs personally, they were actually a great experience.
- Rising practitioners can benefit the most from Security Essentials (GSEC). The SANS class behind it – SEC401 – was one of my most favorite academic experiences. I learned a great deal early on in my career and got behind a five hour test for the first time in my life. It was fantastic, honestly.
- Non-government or transitioning military personnel should consider Cyber Threat Intelligence (GCTI) for threat intel analysts, hunters, investigators, and the likes. It’s a great cert to have. I have not taken it, so my recommendation comes from my peers.
- While not a specific cred,
GIAC
as an entity has some of the highest respected professionals and content in the industry. I have three GIAC certs personally, they were actually a great experience.
Courses
WIP…
Degrees
WIP…